In our increasingly digital world, smartphones serve as indispensable tools, handling everything from personal communication to financial transactions. As these devices have become more ingrained in our daily lives, so too has the need for robust security measures to protect sensitive data. However, a recent study conducted by researchers at Graz University of Technology (TU Graz) has unveiled alarming vulnerabilities in the Android kernels of various smartphones. These vulnerabilities could potentially expose users to known attack strategies—termed one-day exploits—despite the presence of purported protective mechanisms.
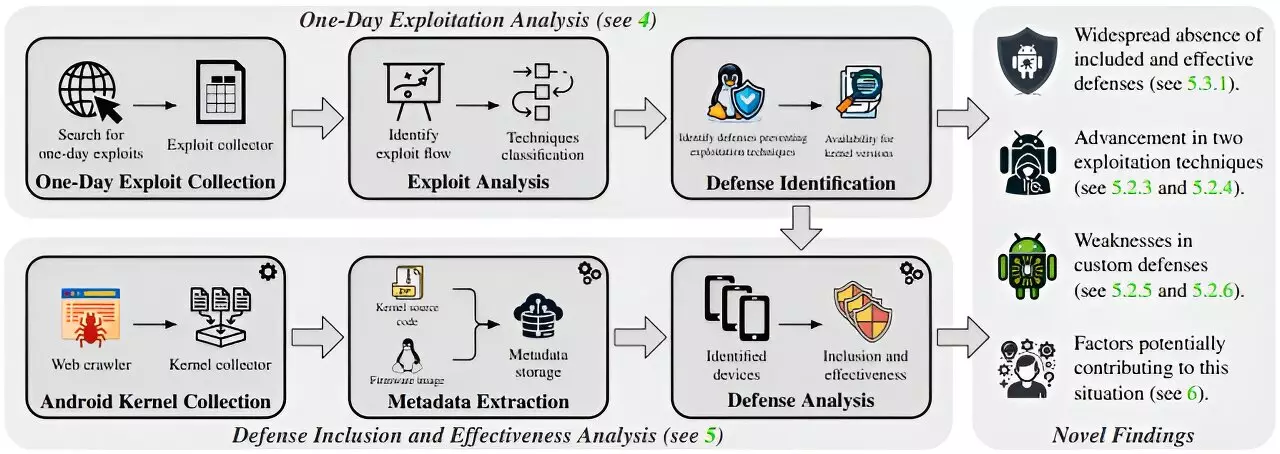
The TU Graz team, including Lukas Maar, Florian Draschbacher, Lukas Lamster, and Stefan Mangard, scrutinized the Android kernels from ten leading smartphone manufacturers, focusing on devices released between 2018 and 2023. Their research, which was unveiled at the Usenix Security Symposium in Philadelphia, encompassed 994 individual smartphones and assessed their abilities to thwart attacks.
The results were striking. Depending on the manufacturer, only a disappointing 29% to 55% of the tested devices demonstrated effective defenses against known exploits. This starkly contrasted with Google’s Generic Kernel Image (GKI) version 6.1, which managed to thwart approximately 85% of attacks. The analysis revealed that manufacturer-specific kernels performed shockingly poorly, being up to 4.6 times less effective than the GKI in defending against threats.
The Implications of Kernel Versions on Smartphone Security
A deep dive into the kernel versions employed by various smartphones unveiled critical discrepancies in security postures. The study assessed Android versions 9 to 14 and kernel versions ranging from 3.10 to 6.1. The findings indicated that manufacturers utilizing older kernel versions tended to provide a weaker security landscape. Intriguingly, the researchers noted that even a 2014 kernel version (3.1) with all security measures activated could outperform many modern kernels crafted by manufacturers, suggesting a severe lack of proper configurations and security activations.
A Comparison of Low-End and High-End Models
Another noteworthy aspect of the research was the vulnerability disparity between high-end and low-end models. The study established that low-end smartphones were approximately 24% more susceptible to exploits than their premium counterparts. The reason for this alarming trend is primarily economic; manufacturers often disable security features in lower-tier devices to preserve hardware performance and minimize costs. This compromises the integrity of such devices, leaving users at greater risk of potential attacks.
In light of these findings, the researchers expressed hope that their insights would galvanize smartphone manufacturers to enhance the security features embedded within their kernels moving forward. They diligently shared their analysis with the manufacturers involved in the study, leading to notable acknowledgments from several companies, including Google, Fairphone, Motorola, Huawei, and Samsung. Some of these manufacturers have reportedly begun to implement patches in response to the vulnerabilities identified.
The researchers have also pressed for updates to Google’s Android Compatibility Definition Document (CDD), which outlines security standards for Android devices. This call for action reflects a broader concern within the tech community regarding the necessity for higher security standards across all smartphone models.
The Path Forward for Android Security
As cybersecurity threats continue to evolve, so must the strategies employed to defend against them. The findings presented by TU Graz highlight a critical gap in smartphone security, exposing vulnerabilities that could endanger user data across a multitude of devices. This underscores the importance of manufacturers investing in improved kernel security measures and ensuring that these defenses are activated and optimized for all models, regardless of their price range.
The study not only highlights pressing issues surrounding Android kernel vulnerabilities but also offers a chance for industry stakeholders to forge a path toward heightened security. As consumer reliance on smartphones grows, the imperative for stringent security measures cannot be overstated. It remains to be seen whether the call for substantial changes will lead to meaningful action, but the recent revelations make it clear that the time for reform is now.
Leave a Reply